Application of Social Engineering in Hacking: A Password-Triggered "Tragedy"
Night Fire: An article I saw on cn_Justice has let us realize that social engineering (shortened as "SE") is not only useful for cracking passwords, but when truly applied, it can be extremely terrifying. As the following article shows, after reading it, you might feel a chill down your spine. By the way, this is an article from the 0712 issue of Hacker X Files, where there's also an article I submitted, though it doesn't have much technical content—just some small Windows application tips. What I want to say is: I still haven't received my sample copy of Issue 12!! It's already January 3rd, and my sample copy... I should probably buy Issue 0801 already~ When I contacted sagi, they ignored me, sweat~ Alright, enough chit-chat. Now read the article; although it's quite long, you'll learn a lot if you finish it. If you want to see more applications of social engineering, I recommend checking out the collection in this blog titled "The Art of Deception" [Complete Chinese Version][DOC][PDF], written by Kevin Mitnick.
Information Source: Evil Octal Information Security Team (www.eviloctal.com)
Article Author: fhod
Note: This article was published in the 12th issue of Hacker X Files in 2007. Please credit the source when re-posting!
PS: Because it's been a while, some details and evidence are no longer available... So part of the following is based on my recollection... Fans of SE might think about it as they read along and figure out whether I'm making up the story or not... If you're new to SE and don't know much about it, just consider this as a novel for now...
Cause of Incident
One accidental opportunity... while helping a friend steal someone's QQ account, I found out that the number was given by another person, her current boyfriend. By checking the comments on a female's QQ space, we confirmed that QQ number 198***2 belonged to her boyfriend. At first glance, it looked similar to my QQ number—it was a birthday number. The profile said "a retired heavyweight hacker." Since the female's QQ number had five digits, and his was also a birthday number, and he claimed to be a hacker, I initially didn't believe him. But I thought I must get this birthday number and this five-digit number.
So, I started investigating 198***2. At the time, I happened to have server permissions for a local forum, and since he was an active internet user, he must have been on this forum too.
I executed the following command in the database:
SELECT * FROM [Dv_User] where [userim] like '%198***2%'
This command queries all users whose QQ information contains 198***2. Two IDs were obtained: Ningning and Wo Ben You Qing.
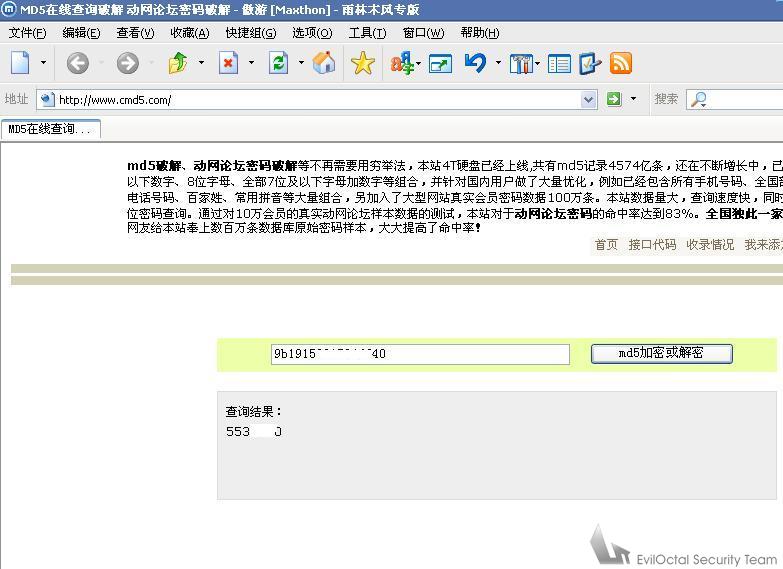
I got the MD5 encrypted password... which I decrypted at http://www.cmd5.com/ to reveal the plaintext password as 553***0.
Figure 1
I logged into the forum with the obtained password, reviewed all his replies and messages sent on the forum, but couldn't find any valuable information.
This password, without looking, was obviously a phone number, likely his home phone. Luckily, I had telecom data, so I could check all local family phones. Entering this number, I found the result... Figure 2
"Chen Mingxin" was very likely his father's name, which was later confirmed during further investigation.
I have a habit... regardless of which QQ, I like to check their profiles from the dating center because some people lack security awareness, so the truthfulness of the information provided is over 80%. However, now directly viewing from Q will prompt you that you're not a premium user... some information can be seen, some cannot... so I captured part of what I could see, constructed a URL, and wrote a small program for future queries. This case was no exception.
Figure 3
Photos, birthdays, and other information were easily obtained this way. It was again confirmed that this QQ was absolutely his birthday number because the birth year and month filled in matched the QQ digits. Due to privacy issues, the images have been processed. Some might say that just based on QQ and the entered birthday, it can't completely confirm he was born on that day... because his profile mentioned being a "hacker"... so these details might have been filled according to his QQ... I suspected this too, but later during evidence collection, I got his ID number, confirming this point.
In his detailed profile personal homepage, I saw this address http://b**n.51.com/, then opened it... trying the forum password I found earlier... many people have the habit of using one password... and this so-called "heavyweight hacker" was no different... login successful...
Figure 4
In his album, I found a very valuable piece of information.
Figure 5
Level 4 Computer Certificate... when I first saw this, I thought this guy was really impressive... but later proved he actually knew nothing... how did he get this Level 4 certificate? Maybe it's a fake certificate, or maybe someone took the exam for him... let's not go into that.
From this certificate scan, I obtained the name "Chen Ning" and ID number: 342126198*****0176. This also proves that the previously found "Chen Mingxin" is very likely his father.
After having one experience of correct password, I tried using the password 553***0 to log into QQ... unfortunately, it was wrong. Since the password was incorrect, I decided to help him change it...(when I did this, QQ's password recovery system was different from now). First, I tried recovering the password to see what his password hint question was... Question: What's my name? Answer... I tried writing his name "Chen Ning"... the result was sent to the secure mailbox... but I didn't know the mailbox address... so I continued collecting information.
Based on the address http://b**n.51.com/, I found two more: http://b**n**2.51.com/ and http://b**n***0.51.com/. From the registration information of these web pages, I got his mobile number 138567****0, Little Smart Phone 0558522***5, EMAIL: c***[email protected]. Trying the obtained password to log into the email... unfortunately, it was wrong...
Try finding the password back... Account is c***t, and we know the birthday... passed smoothly... the question at the time seemed to be the same as QQ... anyway, I changed his password... operation once was already modified back by him... Figure 6
However, after logging into the mailbox, I did not see the confirmation letter sent by QQ...
Continue searching c***[email protected] on Baidu... Figure 7
Based on the information returned in Figure 8, I learned that he worked at XX Hospital. Contact number: 0558-51***95 Fax: 0558-55***70
The information in Figure 9 also confirmed that he indeed works in the management department of XX Hospital.
Now I have gathered enough information... so I plan to appeal his QQ... everyone knows appealing QQ requires knowing his five or fewer friends and historical passwords... Historical passwords I can try using 553***0, but I don't have friends yet... so I browsed his QQ space and QQ photo albums, choosing a few friends from his comments... For the ID number, I used the ID number I obtained earlier... Name is also his own... The appeal result was sent to my EMAIL... In the evening, I checked my EMAIL... the result was out... Appeal successful... I was excited and quickly changed the password to log into his QQ.
In the QQ network hard drive, I found some files... Figure 10
This guy seems to be a police officer too... before checking, he was in the management department of a certain hospital... I wonder how many jobs he has...
By reviewing some emails in his mailbox, I found another EMAIL address b**n5*[email protected]... because it was a letter from Taobao... this EMAIL is likely his Alipay account...
Let me check some information about this EMAIL...
https://www.alipay.com/trade/i_credit.do?email=b**n5*[email protected]
Figure 11
Got the real name "Chen Ning"... so much evidence indicates that his real name is indeed "Chen Ning"... Generally, when I get someone's EMAIL, I like to use Alipay to check if I can get their real name... In several chats with friends, they were all puzzled about how I got their real names and birthdays... After reading this article, you probably know how to do these things now...
Let's use the 4199 virus author as an example... His information I also investigated for quite some time... which has already been disclosed in the 4199 virus bar...
Because the nature is different, here the pictures and information will not be processed.
https://www.alipay.com/trade/[email protected]
Figure 12
At this point, the investigation about him is over... QQ is already in hand... Then, coincidentally, my friend asked me to help deal with the five-digit QQ 4***3 online... So I chatted with her, trying to deceive her... and quickly made a webpage Trojan... disguised it... Because they are lovers... I said it was my love confession... a gift for her... Unfortunately, I was too eager and didn't know what antivirus software she used... Also, the Trojan wasn't processed for bypassing antivirus... She replied saying there was a virus... I had to say sorry... I sent the wrong thing... Perhaps this rash action already aroused her suspicion... So I quickly went offline...
The next day, I found the password had been recovered, and the password protection was changed to... Who do I like? Because of the three 51.com homepages I found earlier... I learned the girl's name was "Wang Juan"... Tried to recover it... Ha... Good luck... Prompt sent to the secure mailbox... But I still don't know the mailbox address... So I continued appealing... In the afternoon, the mailbox received a confirmation letter from Tencent... Quickly changed the password... Damn, the data was also changed... Cursing who stole his number... I helped him modify it... "Is this what you call a heavyweight hacker?" Then I sent another page to QQ 4***3 saying it was done this time... definitely no virus... Then went offline... A day later... when I tried to log in again, I found the password was changed again... So I appealed his number back... After four successful appeals... I was a bit confused... How could he recover it so fast...
And at this point, my friend and QQ 4***6 reconciled... and no longer required stealing her number... And I've already played enough... So I added QQ 198***2 and asked him how he recovered his QQ so fast,
This guy said he was a Tencent technical supervisor... No matter how I stole his number, it was useless... He also said he worked remotely for Tencent... daily wage 500 yuan... I asked what he did at the Public Security Bureau... He said he was a cyber cop... Then I asked how he became a cyber cop... He said in 2005, he hacked our local telecom bureau and stole all ADSL users' points... causing the telecom bureau to lose millions... Later, one day, he turned himself in after drinking too much... Initially, I really believed him... Then we became friends... chatting about technical stuff every day... But the frustrating thing was... every time I asked him something, he avoided answering... Sometimes answered slowly... answers weren't satisfactory...
At the time, my friend nowthk (unfortunately, nowthk has already been caught) and I hacked some game boxes... We were both playing a game called "Wulin Waizhuan" at the time... Coincidentally, this "Chen Ning" was also playing with me in the same area... So I told him I had stolen a lot of game accounts from this area... Equipment and money were no problem... Initially, it was fine... I gave him some accounts to let him strip them... Later, it was his birthday... He invited me to dinner... So I went... In the following days, he often invited me out for dinner and other activities... Asking me face-to-face how I did it... Believing him, I gave him the backend and password of the box... A few days later, nowthk asked me... Did I touch accounts from other areas... I said no... He said it was strange... The buyer he cooperated with had all their accounts wiped... The password was known only to the three of us... So I became suspicious of him... Asking him, he didn't admit... Plus, he avoided technical discussions... I decided to investigate him again...
First, I used an internal vulnerability in EST to create a web Trojan... (written by my invincible wife Mika)
Figure 13
It was tested to work... Then I logged in using a webshell and added an iframe to the box login page. Afterward, he asked me for the login password... I gave him a fake one... Not long after, Gray Pigeon prompted that a host was online... He was infected.
Opening the remote monitoring of Gray Pigeon, this guy was still guessing the password... completely unaware that he was under my control... Hearing him bragging all the time, this time I decided to mess with him... First, I turned on his video... Ha, he noticed... Staring at me... Then I controlled his mouse... Not long after, he sent me a message saying his computer was hacked... I pretended not to know and asked him... Impossible, you're so good, who would dare hack you... He was chatting with a girl from Zhejiang at the time... So he casually told me it was from Zhejiang... Saying he had a tracker running... Anyone hacking him would be known... But he had no idea all this was under my surveillance and I had screenshots...
Figure 14
Of course, I wanted to see this amazing tracker... Watching him download a tracker from Skynet... Download address:
http://users.skynet.be/submissionz03/ntp325.zip
All this, of course, escaped not the surveillance of Gray Pigeon...
Figure 15
After downloading, he renamed the file to "Tracker.zip" and sent it to me... Saying he would go to the restroom first... Using the monitor, I saw he was still guessing the backend password... Truly hardworking...
Figure 16
Since I had such an amazing tracker in hand, I had to see what it was... Otherwise, I wouldn't be worthy of this "heavyweight hacker's" efforts...
Figure 17
I won't explain the software's usage and introduction... If you don't know, Google it...
During the following days of monitoring, I found out that the messages in the box were indeed tampered with by him... And he auctioned them on 5173.com... So I activated the keylogger of Gray Pigeon...
Figure 18 is recorded by the pigeon
The username on 5173.com is b**n, and the password is the same as 553***0
Log in to verify if it's correct... Figure 19
Since I couldn't keep monitoring him every day, for convenience, I uploaded another keylogger... Automatically generating a file on his C drive and saving all keystrokes.
A few days later, checking the keystroke records, I found this guy applying for a job at Tencent Photo System... Figure 20
No wonder he told me he was a Tencent technical supervisor... After applying, he sent it to me to look at... The picture exposed his ID number again...
Figure 21 is his username and password on the Tencent Photo System. Among them, 138567***10 is his personal mobile phone number (this was also obtained during the first investigation)
I had already obtained his Alipay account as b**n5*[email protected]. Let's try logging into Taobao with the password 553***0 to see if it's correct...
Figure 22 Login successful... Again, this stupid password... Its contribution is huge... People who have used Taobao should know that Alipay is linked to bank accounts... Continuing to pursue might get his bank information... Log into Alipay... This password is wrong... But it provides a password recovery function... Figure 23
Unfortunately, this answer is incorrect... Figure 24
But this error prompt helped me a lot "If you forgot the answer to your security question, please click Input ID Number"
I'll try another way to recover it... Since I already know his ID number... Try to see if it's correct... Figures 25 and 26 Password recovery successful and sent to the mailbox...
Mailbox password is unknown... Same as before, use password hints to recover... This time, his question was "What's my name?" Answer..."Chen Ning" is wrong... Just tried "Ningning"... (Later, I used this answer to try Taobao's too, and it was successful)... Successfully modified the password... Log into the mailbox with the modified password...
Figure 27
Use the link in the mailbox to modify the login password... Same method to recover Alipay payment password... Figure 28
Log in and check Alipay account information... Figure 29 Very unfortunate, bank information is invisible...
Don't forget we still have a 5173 unused... Those who have sold game equipment on 5173 should know... When the transaction amount reaches a certain level, you can apply for withdrawal... In his previous withdrawal records, I got his bank card number as "9558801311******106";
Next step is to get his bank password... Through Gray Pigeon remote monitoring, I know his password is 7 digits... ICBC's password must be a combination of numbers and letters... This time, it's purely guesswork... With so much information already obtained, it's not difficult to guess the password... After several guesses, the password was figured out as "b**n**2"... His ID plus birthday... Also his game account in Wulin Waizhuan... The game password of Wulin Waizhuan was also obtained by me... Though I didn't mention it before...
Check the screenshot after successfully logging into the bank! Figure 30
That's it for this matter... We have obtained his name, birthday, mobile, telephone, workplace, EMAIL... Father's name... Several 51 accounts and passwords... 5173 account... Alipay... Bank account and password... Quite a substantial harvest...
Long after, due to some other matters, we quarreled again... This time, I sent him all the results of my investigation... I guess he must be pretty frustrated... Before, I always pretended not to know his background and kept my distance... After sending him those screenshots and evidence, this guy had nothing to say...
Figures 31 and 32
I believe after reading this article, you must feel incredibly astonished... Actually, the entire SE process was completed solely because he used the same password everywhere... Just because of such a dumb password, I was able to so easily obtain all his passwords... Of course, the harm brought by social engineering isn't limited to this...